Security is a bit like your basic utilities like electricity, heat, and water: you don’t think about them much and maybe even take them for granted until they’re gone. Then you suddenly realize how critically important they are. In fact, piracy alone can have significant financial impacts. In the United States alone, GDP losses due to piracy estimate between $47 and $115 billion.
Security considerations impact everything we do at Brightcove. From product development to video management, our focus is to ensure that our customers are successful. From playback restrictions to data security, customers can uphold brand integrity and see a return on investment.
Whether content is for an internal or external audience, free or monetized, Brightcove keeps content and data secure while still allowing viewers to access it from any device, anywhere in the world. Our policies ensure that internal content remains confidential, external content is effectively monetized, and your brand maintains its integrity.
A COMPREHENSIVE APPROACH TO SECURITY
We make video readily available to anyone who should see it – and inaccessible to anyone who shouldn’t. But our approach to security is much more comprehensive than simply securing a video. At Brightcove, security is built into every step of our operations, from office security protocols and employee compliance certification to product development and content management.
Brightcove’s software-as-a-service (SaaS) video platform has a broad set of functions that help customers scale and manage their video content securely and reliably. Our data is hosted in a multi-tenant environment, but segregation is integrated at the customer level, as this image shows:
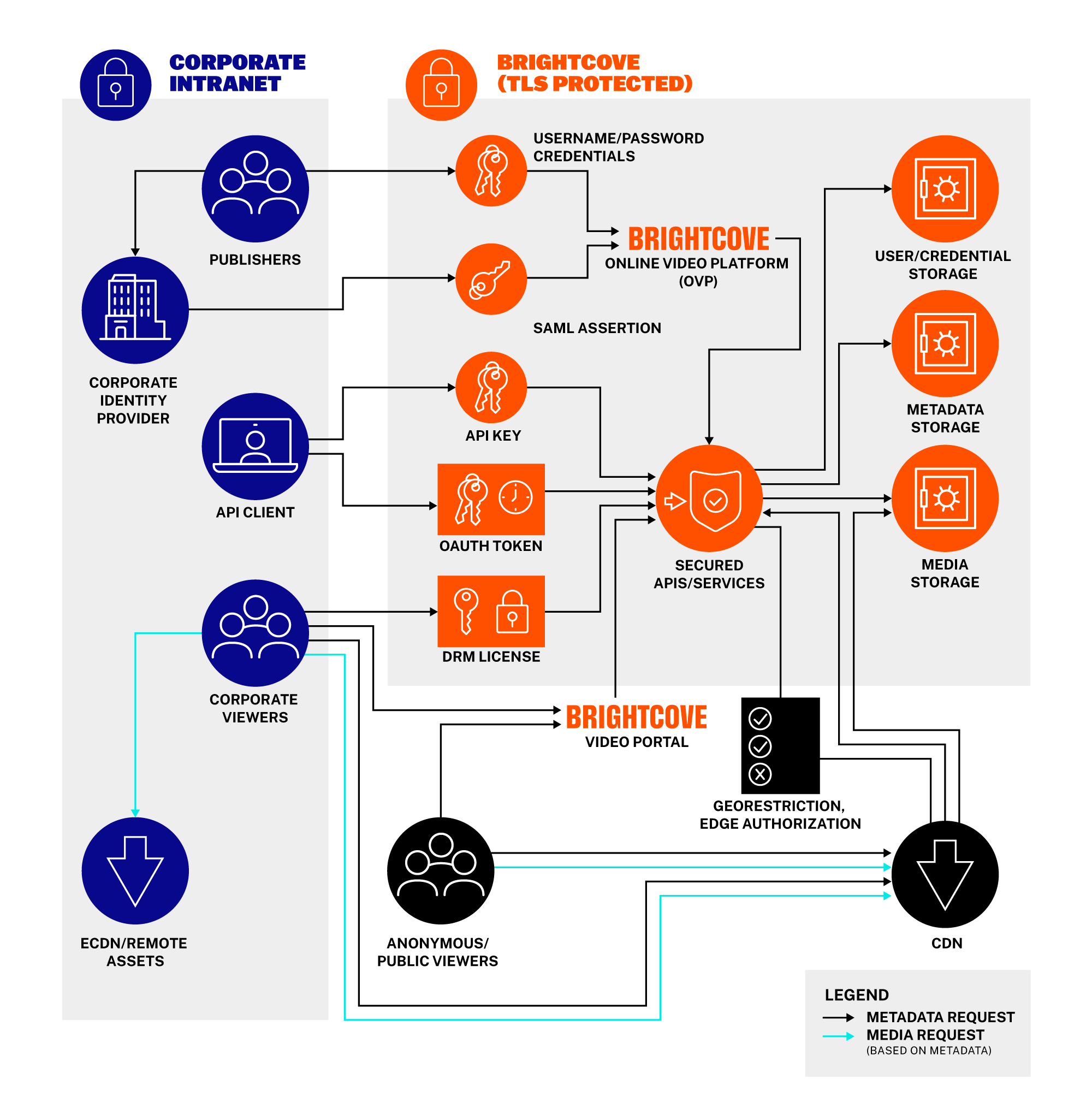
For added security, the Brightcove platform also offers the option of storing master videos only in a region selected by a customer. For example, if a customer is tied to us-east-1, the content delivery network (CDN) located on the East coast of the United States, their masters wouldn’t leave us-east-1 – this is critical to ensuring compliance with regions that require data to stay within certain geographic areas.
MAKING MEDIA CONTENT MORE SECURE THAN EVER
Content creators need to be ever-vigilant about securing their content, from ingestion through playback. There are many levels of security that can be implemented such as restricting assets (the content itself), handling viewer access/permissions (implement rules around how audiences are able to view the content), and prevention of content piracy.
We recently introduced a new set of features called Brightcove Playback Restrictions, our most advanced security offer for the online video market, which address content security at every level.
PROXY RESTRICTIONS
These restrictions block playback from a variety of potentially risky IP scenarios:
- ANONYMOUS: The IP address of the client is not available. This includes services that change location to beat DRM, TOR points, temporary proxies, and other masking services.
- PUBLIC: Multiple users proxied from a location allowing public internet access.
- CORPORATE: Generally considered harmless, but location can be a concern. You can set up rules around scenarios where multiple users are proxied through a central location or locations while sharing a single network-apparent IP address. Example: Employees could use the Boston or Tokyo VPN; multiple users would be using that same IP.
- TRANSPARENT: The IP address of the client is available via HTTP headers, though the value is not necessarily reliable (e.g., it can be spoofed).
MID-STREAM RIGHTS CHECK
After the initial rights check is run at the start of video playback, another validation of the viewer’s credentials is run mid-stream. If the mid-stream check fails, the player will stop video playback. A great example of this is for a paid sporting event: if the team has a limit on stream concurrency and a paid viewer shares their login, a mid-stream check would determine the user no longer meets the conditions of the restrictions (i.e, more than one person has signed in with those credentials) and playback would stop.
STREAM CONCURRENCY
Limiting concurrent streams per user discourages viewers from sharing their credentials with friends who don’t have accounts. With concurrent stream limits, you define the number of video streams that a specific user can watch at any given time.
DEVICE REGISTRATION
Device registration occurs when a DRM license request is made. A unique ID is assigned to each device, and with each license request, the device limit is checked and enforced. An example of this is when a content provider grants a publisher permission to stream their content for a period of time, and their contractual agreement limits the number of devices associated with a single viewer to two. Once that limit is reached, if a user tries to view the content on a third device – say, a connected TV – the playback will be denied. This enables content owners to achieve their monetization objectives and minimize unauthorized access.
COMPLIANCE REQUIREMENTS
Brightcove follows a secure platform development model that includes enforcing encryption standards for all data in transit, employee compliance with documented data storage protocols, and user authentication when using the product.
We need to ensure that our customers and our company are completely protected when compliance requirements change. As part of our security strategy, we engage third-party security research firms to perform an annual vulnerability scan and penetration testing, including:
SARBANES-OXLEY (SOX) COMPLIANCE
Brightcove proactively obtains third-party audits to review controls, policies, and procedures. A review of a company’s internal controls is often the largest component of a SOX compliance audit. Internal controls include all IT assets, such as computers, network hardware, and other electronic equipment, that financial data passes through.
INDUSTRY CERTIFICATIONS
Digital Production Partnership (DPP): The DPP “Committed to Security” program enables broadcast and production suppliers to demonstrate their commitment to achieving security best practices. Privacy Shield: Privacy Shield certification reflects our pledge to our customers that we maintain adequate safeguards and comply with the Privacy Shield principles for transfer of European and Swiss personal data to the United States.
DATA SECURITY
Beyond playback, companies that offer robust analytics should provide equally comprehensive features to secure those data points. With Brightcove Audience Insights, we employ several security policies to protect our customers’ data.
SECURE PROTOCOLS
When retrieving data from a partner system or a customer’s datastore, we use secure protocols like HTTPS or SFTP. Once ingested, customer data is sequestered in an S3 bucket with limited access granted, even to our employees. After the data is harmonized, accessing the API or Brightcove Audience Insights requires a robust username and password that sets a temporary session cookie for each user.
NECESSARY DATA
We only pull data we need. Everything else is left behind in the customer or vendor system. In the event of an accident or malicious act, we cannot lose control of something we do not have.
PSEUDONYMIZATION
With the introduction of the GDPR standard in 2018, the concept of pseudonymization became a global policy for Brightcove. While we normally avoid collecting PII, there are a few use cases that require an email or IP address. Per GDPR, this data is immediately encrypted upon ingest using a one-way hash. The source data is deleted. There is no way back from the hashed result to the source data.
CLOUD STORAGE
Physical access to the data storage device is always a concern. This is where using a cloud-based service like AWS has its advantages. Access to the AWS data centers is strictly guarded and their architecture makes it near impossible to tell which data is on which server or storage array.
DEVELOPMENT AND DEPLOYMENT STANDARDS
Brightcove has established SDLC processes to ensure delivery of quality software services. We use an AGILE-based planning process, version control, automated testing, and automated deployment. Automation ensures not only reliable delivery but also an auditable process based solely on the resources noted in our version control system.
TEAM RESPONSIBILITY
Since we are only as strong as our weakest link, each teammate at Brightcove is reminded that they have a responsibility to speak up if they have a concern. It’s better to delay a release and even miss a deadline if a little extra time allows us to test a potential weakness and ensure our security standards remain strong.
THE RISING IMPORTANCE OF SECURITY FOR ENTERPRISES
When most people think about enhanced security, they usually envision some kind of media-related use case. But today, that’s simply too limited, and many enterprise organizations are seeing the need for enhanced security.
From confidential town hall meetings to big-budget virtual events, security plays a crucial role in safeguarding your brand and ensuring you maximize ROI.
Brand integrity is the lifeblood of an enterprise, and a breach of internal information or communications has a significant impact on a brand’s integrity. In one recent example, an unwelcome guest infiltrated the internal town hall of a well-known fast food brand. The announcements made at the town hall appeared in the next day’s news, causing the organization significant negative publicity and even exposing them to legal impact. The brand is now working with Brightcove to protect their internal communications from unauthorized access through user permissions and link-sharing prevention.
Events represent a major expense for companies, and securing a return on the significant sums invested in them depends on the ability to control who can attend. If you’re charging for admission or for access to premium content, it’s essential that every attendee pay the appropriate amount. No one should be able to share logins or links to content with people who haven’t paid for it. Brightcove security measures will enable you to maximize your ROI for every event.
PEACE OF MIND
In today’s world, it’s critical to be able to connect with everyone who is important to your business, but those connections must be completely secure. And Brightcove’s extensive industry-leading security measures gives you the confidence that they are.
With Brightcove, you can implement rules regarding how audiences are able to view your content and on how many devices. You can set concurrent stream limits and prevent link sharing. If piracy is a concern, you can ensure that viewers can’t copy content and share it with others. You’ll be in control, and you’ll never worry about security again. Not because it’s unimportant, but because you won’t have to.
Want to know more? See our security features page to stay up to date on our latest security efforts and see how Brightcove can help.




